SSH for authentication#
Topic learning objectives#
By the end of this topic, students should be able to:
Describe how SSH authentication works
Setup and use SSH authentication as the authentication method for working with GitHub
The secure shell protocol (SSH) for authentication#
So far you have likely been using a personal access token to authenticate to GitHub. This works, however there is another very secure and more convenient method of authentication that is widely used: secure shell protocol (SSH). SSH can be use for other forms of authentication as well (beyond GitHub), including logging into remote machines in the cloud. So for many these reasons it is worthwhile learning. Thus, we will spend some time explaining it here, and setup our computers to use this for authenticating with GitHub going forward.
Remotely accessing another computer using SSH#
Let’s start with some definitions:
Definitions#
Secure SHell (SSH) - a common method for remote login to another computer which is secure.
server - a machine you are SSHing into. The server sits and waits to be contacted.
client - usually your machine. The client initiates contact with the server.
SSH key-based authentication#
Two components:
public key
private key
These files have an asymmetrical relationship:
the public key CANNOT decrypt messages generated by the private key
the private key CAN decrypt messages generated by the public key
Understanding public key private key concepts#
Think of a public key, not as a key, but as a padlock that you can make copies of and put anywhere you want.
To put your ‘padlock’ on an another machine, you would copy it to
authorized_keysin the~/.sshfolder.Think of a private key as an actual key, it can open the padlock that is stored on the other machine.

source: http://blakesmith.me/2010/02/08/understanding-public-key-private-key-concepts.html
How the lock works#
Keys are generated using
ssh-keygen, to make private key (usually calledid_ed25519) and a public key (usually calledid_ed25519.pub)You can make copies of
id_ed25519.pub(public key/padlock) and distribute them to other machinesThe other machine uses the public key to encrypt a challenge message to you
You need to show that you can decrypt the message to demonstrate that you are in possesion of the associated private key
_Note: GitHub has changed recently the SSH key generation instructions to use Ed25519 algoritm.
You can put your lock at many places#
As long as you are using the same lock (public key), you will be able to open it with the same private key.
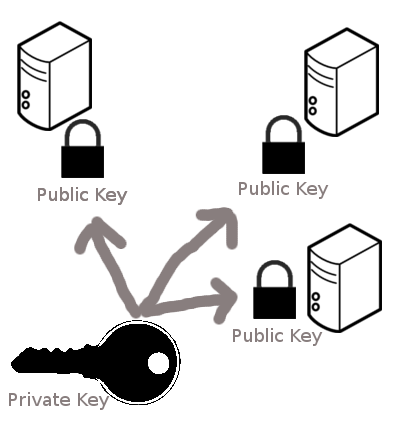
source: http://blakesmith.me/2010/02/08/understanding-public-key-private-key-concepts.html
Keeping your private key safe#
ssh-keygenallows you to put a password or passphrase on the private keythis should be shared with NO ONE!
if your private key does fall into the wrong hands, the person must still know the password or passphrase to use the private key
source - https://xkcd.com/936/
Exercise#
Setting up SSH for authentication on GitHub! Follow the docs linked below here to accomplish each step to set this up. At the top of each of the documentation sections, be sure to select the tab for your operating system.
Test it out! Create a private GitHub.com repository and try to clone it using the SSH code URL (instead of the HTTPS one), it should look something like this:
git@github.com:username/repo-name.git
(whereas HTTPS code URLs look like: https://github.com/username/repo-name.git)
